Last updated: November 4, 2025
The svchost.exe (Service Host) file is a legitimate Windows system component. However, malware frequently masquerades under this name—often with spelling variations or incorrect file locations—to avoid detection by security software.
High CPU usage, system sluggishness, application crashes, or unexpected security alerts may indicate a Svchost.exe Trojan or similar malicious software.
See also: Top 10 Free Malware Removal Tools for Windows (2025 Edition)
Understanding Svchost.exe: Legitimate vs. Malicious
The authentic svchost.exe hosts Dynamic-Link Libraries (.dll files) as services, improving performance and reducing memory consumption.
Identification Comparison
| Feature | Legitimate svchost.exe | Malicious Svchost.exe |
|---|---|---|
| File Location | C:\Windows\System32 (or SysWOW64 for 32-bit services) | Alternative locations (AppData, Temp, Users folders) |
| File Name | svchost.exe (correct spelling) | Misspelled variants (scvhost.exe, svhosts.exe, SVCHOST.EXE.EXE) |
| System Behavior | Stable resource usage; associated with identifiable Windows Services | Excessive CPU/memory consumption; operates without attached services |
Phase 1: System Preparation and Threat Neutralization
Malware employs defensive mechanisms to prevent removal. Execute these steps in Safe Mode to neutralize threats and enable cleaning tools.
Step 1: Disconnect Network Access
Immediately disable internet connectivity by unplugging Ethernet cables or disabling Wi-Fi. This prevents malware from communicating with command-and-control servers, blocking data exfiltration and additional payload downloads.
Step 2: Boot into Safe Mode with Networking
Safe Mode loads essential Windows services only, preventing full malware execution.
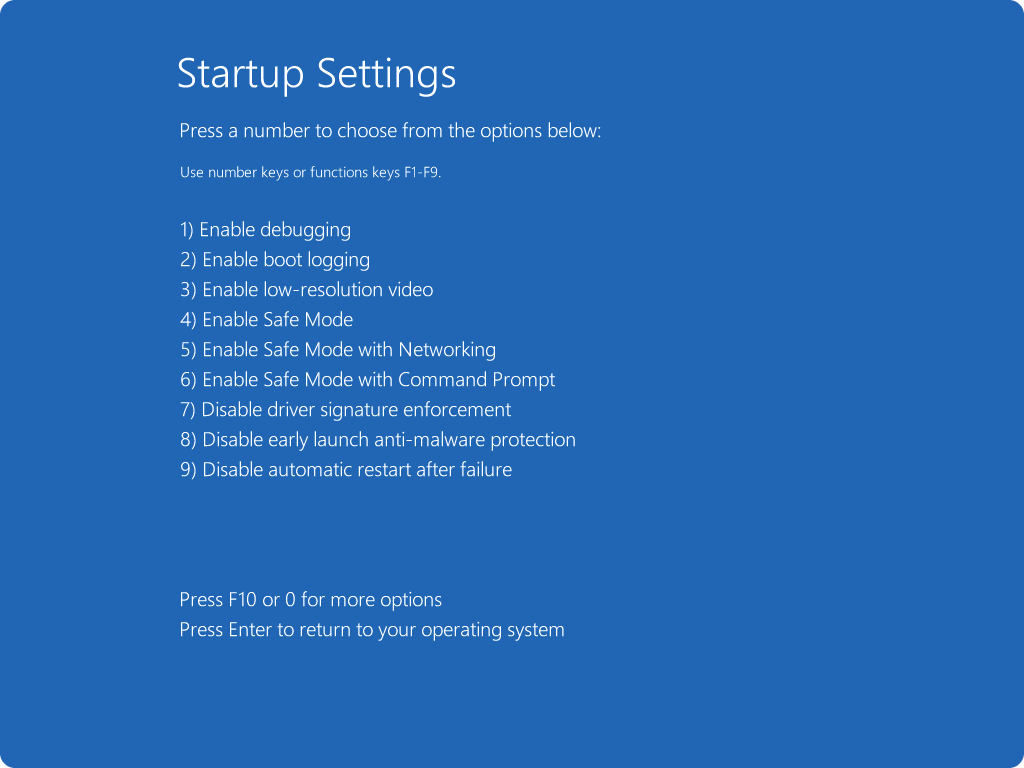
- Click Start > Power
- Hold Shift and click Restart
- Navigate to Troubleshoot > Advanced options > Startup Settings
- Click Restart, then press 5 or F5 for “Enable Safe Mode with Networking”
Note: Networking capability is required for downloading removal tools.
Step 3: Execute Rkill to Terminate Malicious Processes
Malware actively blocks security scanners. Rkill terminates known malicious processes, enabling scanner execution.
- Download Rkill (or renamed version like iExplore.exe) from a reputable source
- Execute the downloaded file; a command window will open, run automatically, and close
- Do not restart your computer—malicious processes will resume upon reboot
Phase 2: Comprehensive Scanning and Removal
Employ multiple specialized scanners to ensure complete malware elimination.
Step 4: Full System Scan with Malwarebytes
Malwarebytes specializes in detecting and removing persistent threats including Trojans and Rootkits.
- Download, install, and update Malwarebytes (free version sufficient)
- Enable Rootkit Scanning in Settings
- Execute Full Threat Scan (may require extended time)
- Quarantine or Remove all detected threats
Step 5: Execute Kaspersky TDSSKiller for Rootkit Detection
Svchost.exe malware frequently employs rootkit techniques requiring specialized detection.
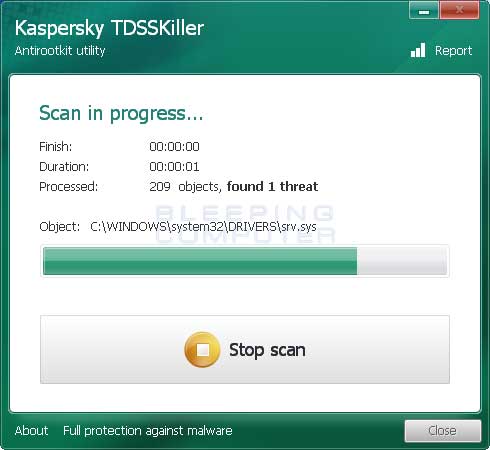
- Download and run Kaspersky TDSSKiller
- Click Change parameters and enable “Detect TDLFS file system”
- Execute Scan and remove identified threats
Step 6: Deploy AdwCleaner for Adware Removal
Adware often accompanies Trojans. AdwCleaner targets browser hijackers, toolbars, and unwanted extensions.
- Download and run AdwCleaner
- Click Scan Now
- Quarantine all identified items
Phase 3: Manual Verification and System Cleanup
Step 7: Identify and Remove Malicious Svchost.exe Files
Manual verification removes files potentially missed by automated scanners.
- Open Task Manager (Ctrl + Shift + Esc)
- Navigate to Details tab and locate svchost.exe processes
- Right-click suspicious processes and select “Open file location”
Critical Assessment:
- If location is C:\Windows\System32: File is legitimate—do not delete
- If location is elsewhere: End Task first, then delete the file from the opened folder
Step 8: Restore Browser Shortcuts and Remove Malicious Extensions
Malware modifies browser shortcuts to maintain persistence through malicious homepages or search engines.
Shortcut Restoration:
- Right-click browser shortcut (Chrome, Edge) on Desktop or Start Menu
- Select Properties > Shortcut tab
- Examine Target field
- Remove any text following the closing quote (should appear as: “C:\Program Files\Google\Chrome\Application\chrome.exe”)
Extension Cleanup:
- Open browser and navigate to Extensions/Add-ons
- Remove unrecognized or unintentionally installed extensions
- Reset browser settings to factory defaults to clear hidden preferences
Step 9: System Finalization and Security Restoration
- Re-enable primary Antivirus or Microsoft Defender
- Restart computer in Normal Mode
- Execute final quick scan with both primary Antivirus and Malwarebytes to confirm system integrity
Conclusion
Following this systematic approach ensures complete removal of Svchost.exe malware and associated threats. The multi-layered scanning methodology combined with manual verification provides comprehensive protection against sophisticated malware variants. Maintain regular security scans and keep antivirus software updated to prevent future infections.


