If you notice suggestive websites opening automatically while surfing the web, your browser might be infected with the Fuq.com virus. No, your computer is not getting horny. (though, I applaud you for such imagination)
Yes, it is a reason to worry. This website is a Browser Hijacker Malware that redirects the victim to the target website. Today we have amassed a detailed guide to help you get relief from this Malware. To remove Fuq.com from your browser, for e.g. Mozilla Firefox, you can follow these steps:
- Start Mozilla Firefox.
- Open the Add-ons Manager by selecting “Extensions” from the menu.
- Click on the Open menu icon and choose “Options.” In the Options window, navigate to the “General” tab.
- Click on the “Restore to Default” button. Then Go to the “Search” section in the left menu.
- Identify the unknown search engine associated with Fuq.com and click the “Remove” button.
Furthermore, it’s essential to understand the potential risks associated with keeping the Fuq.com virus on your system. This malicious software can lead to a range of harmful activities, including opening malicious or infected websites in the background, collecting personal information such as your IP address and geographical location, gathering browser history, cookies, and cache, as well as collecting usernames, passwords, and even sensitive banking details like credit card information.
Table of Contents
What Exactly is Fuq.com?
Fuq.com is a Malware categorized as a “Browser Hijacker.” It is a program that runs in the background, pops up advertisements, and redirects your browser to particular websites in the name of promotion and advertising.
Browser Hijackers have the job of redirecting your browser to those websites for which the hacker is paid. Some webmasters pay for this Malware to direct the browser to their site.
This increases traffic and, ultimately, their ranking in Google. As you might have guessed, Fuq.com is a Browser Hijacker programmed to redirect your browser to this malware site since the hacker is paid for the promotion.
See Also: 10 Best Google Chrome Flags for Efficient Browsing
What is the harm in keeping Fuq.com?
Imagine yourself working on a school project while your parents enter the room, and suddenly the browser is directed to this strange website.
Yes, the horror is palpable.
This alone should be enough incentive to get rid of this Malware. Though, if you are still not convinced, here is a complete list of potential harms a Browser Hijacker can cause:
- Opening malicious or infected websites in the background.
- Collecting personal information like your IP Address and geographical location.
- Gathering Browser History, Cookies, and Cache.
- Collecting Usernames and Passwords.
- Gathering banking details like Credit Card details.
See Also: 4 Best Free VPN for Chrome to Ensure Complete Safety
How did my system get infected?
Browser Hijackers are not applications that can be seen on your desktop. Even some Anti-Virus programs may be unable to detect such Malware since they actively try to hide their presence.
A few ways in which your system could have been infected are:
- Visiting malicious websites which inject such Malware into your browser without your notice.
- Downloading suspicious extensions in your browsers.
- Installing third-party applications from non-trustworthy resources.
- Installed by some pre-existing Malware host.
See also: Remove Svchost EXE Malware.
How to remove Fuq.com?
Follow the steps below to remove this malware website link from your browser.
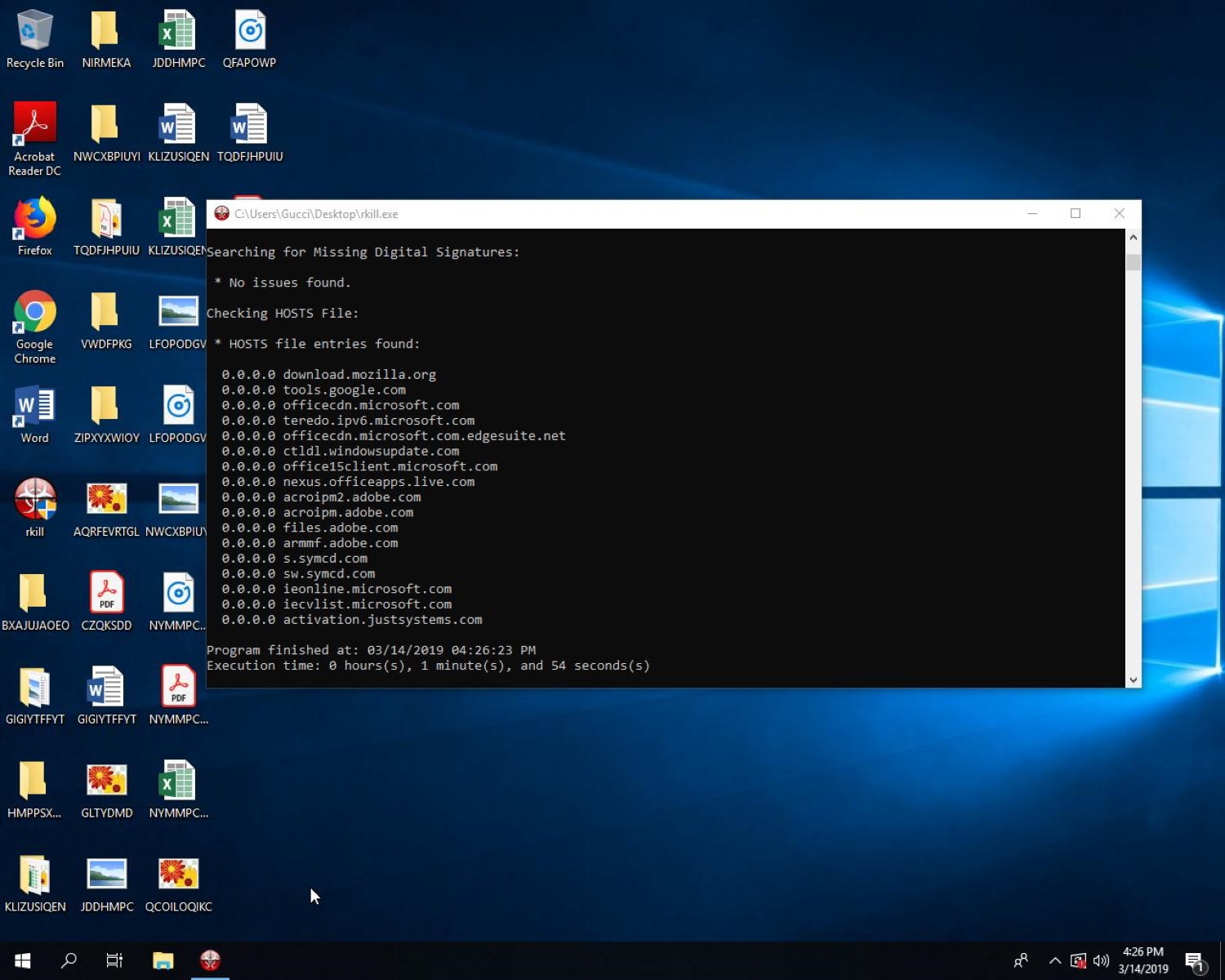
Step 1: Download and run Rkill.exe
Rkill is the silver bullet to completely halt all the malicious processes running at the time on your computer. It is a simple open and close application that automatically kills all the malicious tasks running in the background.
Alternatively, you can open the Windows Task Manager and manually kill all the tasks named Fuq.com. Still, the sheer number of processes and the possible presence of other malicious tasks make it faster and more convenient to use Rkill.
Step 2: Install and run Malwarebytes on your computer
Malwarebytes is a renowned anti-virus program that automatically detects and removes most malicious software that might have infected your device.
It is a simple three-step process to use Malwarebytes to remove all the malicious programs from your device:
- Install Malwarebytes by clicking here.
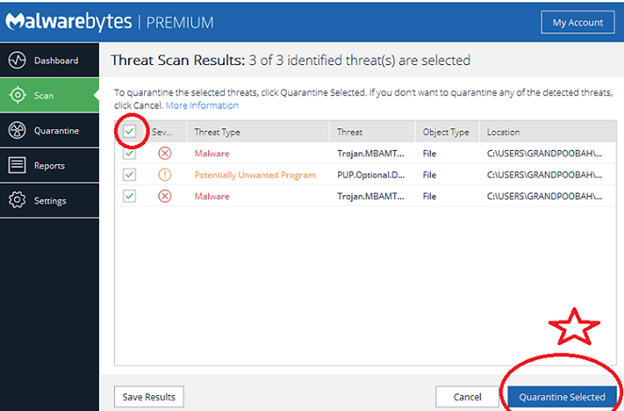
- Run Malwarebytes and click on “Scan.”
- Click on “Quarantine Selected” to remove all the Malware detected by Malwarebytes.
See Also: How to Fix YouTube Black Screen on Google Chrome Easily
Step 3: Cleaning up the Browser Shortcuts
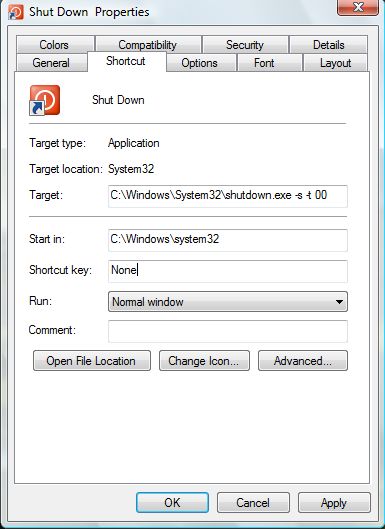
- Right-Click on your Web Browser’s Shortcut. (Google Chrome, Firefox, etc.)
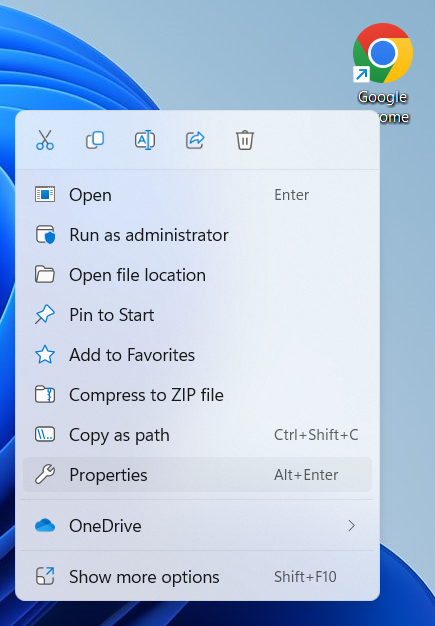
- Select “Properties.”
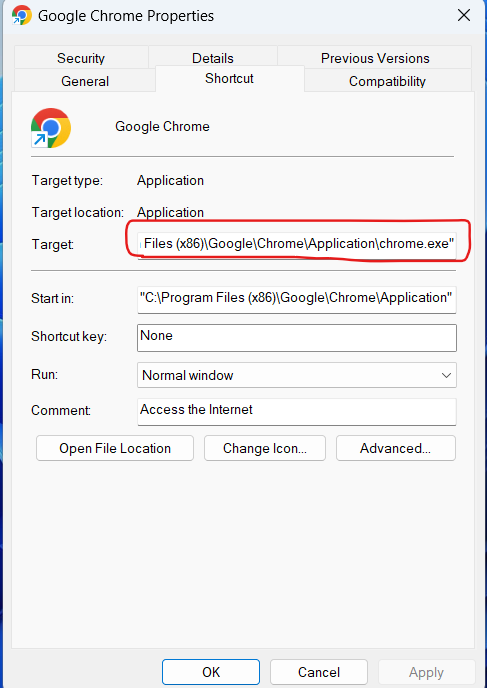
- Under the “Shortcut” tab, check the “Target” section. Then, Remove anything after “.exe.” and Select “Apply.”
Step 4: Quarantining Browsers
Google Chrome
- Close Google Chrome if underused.
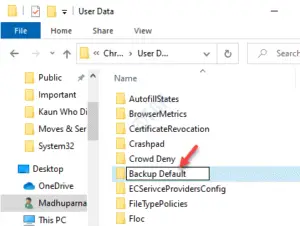
- Go to: C:/Users/<USERNAME>/AppData/Local/Google/Chrome/User Data.
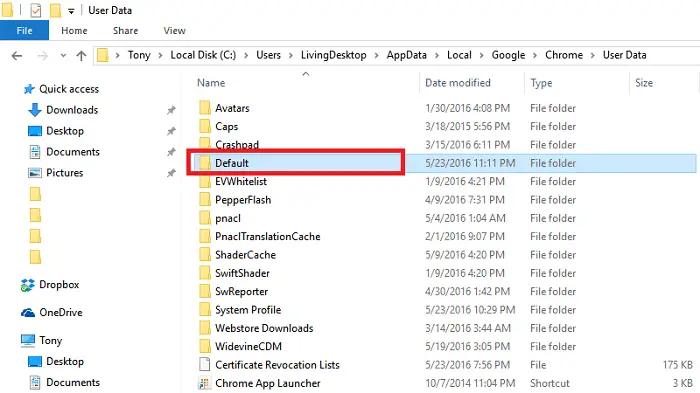
- Rename the folder “Default” to “Backup Default.”
- Restart Google Chrome.
See Also: 4 Ways to Fix Malwarebytes Won’t Open Error {Latest}
Mozilla Firefox
- Open the “Settings” menu. Click on “Add-ons.”
- Select “Extensions” to see all the extensions installed.
 Remove all the suspicious or unknown extensions.
Remove all the suspicious or unknown extensions.
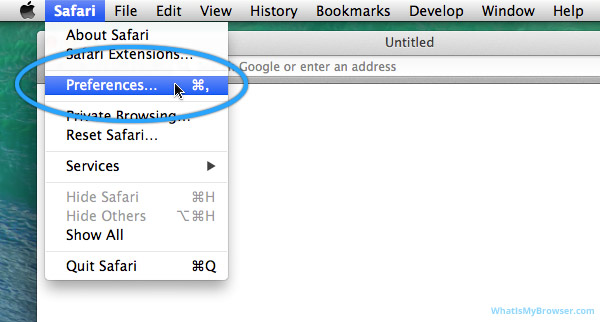
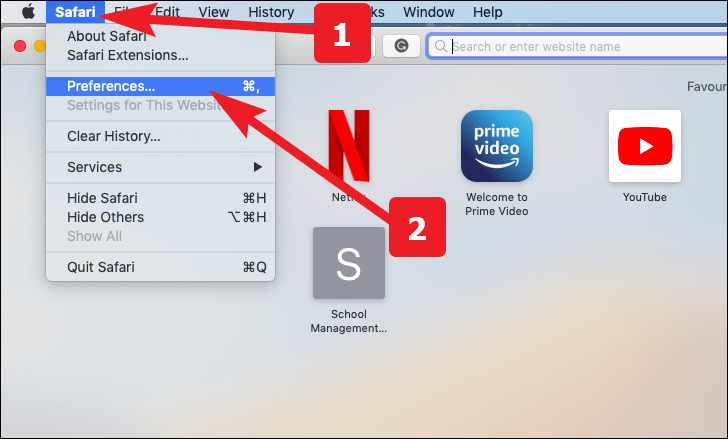
Safari
- From the Safari menu, select “Preferences.”
- In the Safari Preferences window, click the “Extensions” tab.
- Find any unknown plugin, then click the “Uninstall” button.

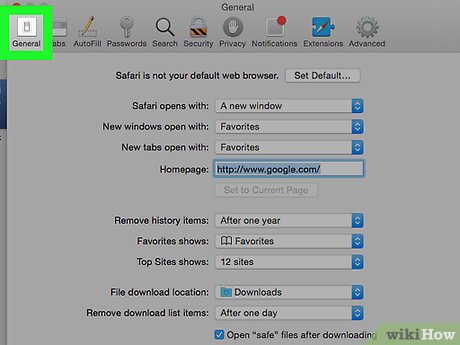
- Next, select “Preferences,“ go to the “General” tab and change the “Default Search Engine” to any trusted Search Engine of your choice like Google, Yahoo, etc.
- Then, in the “General” tab, find the “Home Page” and change it to any trusted website you want as your homepage.
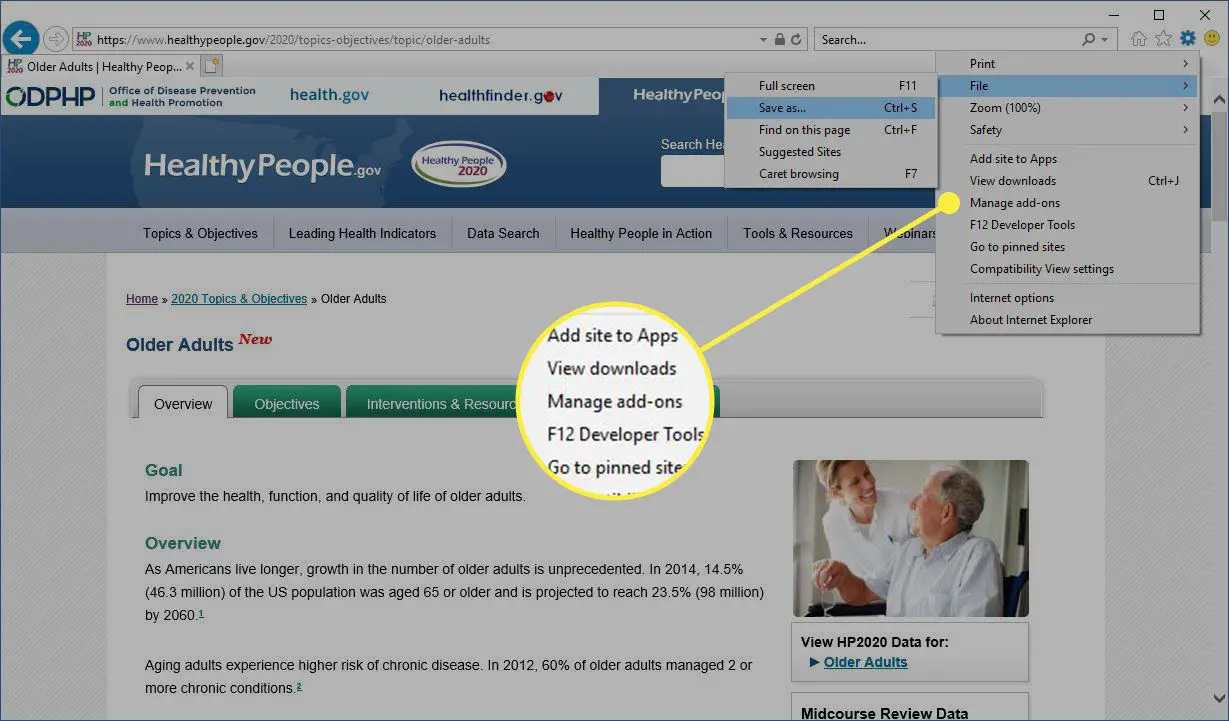
Internet Explorer
See Also: 3 Methods to Remove Win32:Malware-gen Trojan
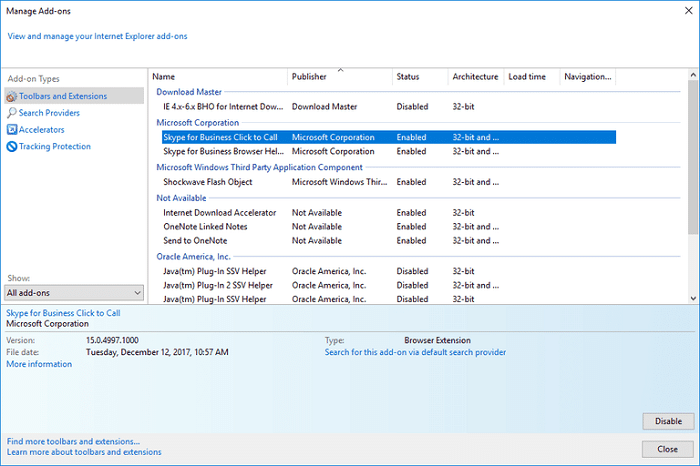
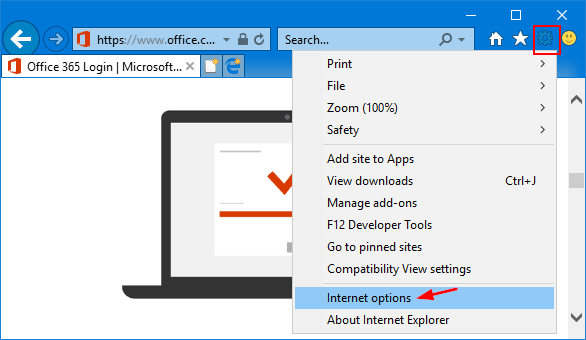
- Go to “Settings” and click on “Manage Add-ons.”
- Change the URL to any of your trusted websites. (like Google, Yahoo, etc.)
Step 5: Restart your computer
Now, finally, restart your system to see the changes.
FAQs
Is Safari a safer option than Chrome?
Yes, Safari is the safer option for protecting user privacy. Regarding staying on top of security risks, Chrome has a minor advantage over Safari. Still, regarding a private surfing experience, Safari has a considerably better track record than Google.
Does a VPN safeguard Safari?
Yes. Your Apple device's entire activity, including any Safari browsing, will be protected by a dedicated VPN program. Safari is one of the safer choices when comparing web browsers. Unfortunately, it does not work on Windows, Android, or Linux platforms; it only works with Apple devices.
Does Safari track your data?
Safari does indeed track your info, but Safari only provides third-party search engines with the bare minimum of data required to execute a web search. For instance, Safari doesn't transfer cookies or location information, tools for tracking users between websites.
How can I use Safari to block dangerous websites?
Open Safari on your Mac, then select Settings (or Preferences) from the menu bar. You can set choices to allow or block some or all pop-ups in the Websites tab. Turn on the warning when visiting a fraudulent website setting under the Security tab.
Can a virus be freed from my browser?
Yes, Google Chrome has an integrated malware scanner to identify and remove malicious programs and files from your computer or browser. When you select Reset and Clean up under Settings > Advanced, Chrome will check your device for harmful software and remove it.
Conclusion
Following the steps given above should ensure the complete removal of this Malware from your system. Scanning your system with a reliable Anti-Virus program is always recommended.
Also, be wary while installing free application packages and choose “Custom Installation” to avoid being a victim of Bundling. We hope it helped!
See Also: 3 Ways to Remove National Consumer Center Virus or Scam