Whether you are home or not, Best Self Monitored Home Security System offers freedom from worry and anxiety. However, the cost or expense for that peace of mind can be high. And you need to both pay for professional monitoring and buy the equipment.
The best Self Monitored Home Security System includes:
- Link Interactive
- Ring Alarm
- Abode Connected Home Security
- SimpliSafe
- Vivint
- ADT
- Wyze
- Abode iota Smart Security Kit
Fortunately, with the surge or influx of home automation devices, in-house monitoring is becoming more popular. In this post, we’ve rounded up the three best self-monitored home security systems in 2023.
Table of Contents
8 Best Self-Monitored Home Security Systems of 2023
Read on to learn more about the Best Self Monitored Home Security System-
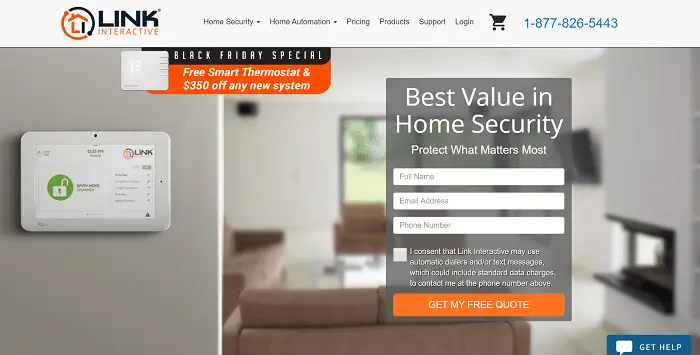
Link Interactive Security System
Link Interactive, serving the people for about sixty years, provides customizable DIY or self-monitored home security solutions. Primarily, there are three plans you can select from. These are the Elite, Gold, and Standard Plans. Additionally, you can pick between two different control panels for each project. Moreover, Link Interactive provides changeable contracts for selecting a one-year, two-year, or three-year warranty. Furthermore, you can acquire a locked-in rate for your chosen arrangement.
Thus, there are no tricks or elaborate deceptions with increased payments. Ultimately, if you are looking for the necessary features for securing your home, the Link Interactive Security System offers you just that. You will have carbon monoxide detectors, fire detectors, smoke detectors, crash and smash alarm protection, a self-monitoring alarm system, and a 4G LTE cellular monitoring connection. Read a Link Interactive security system review online to learn more about this product. It is indeed one of the best self-monitored home security systems.
Visit: Link Interactive Security System
Ring Alarm
In 2018, Amazon acquired Ring, strengthening the notable status of the IOT-based home automation company as an industry leader. Ring’s well-designed, sleek product line-up guarantees or assures further integration and innovation due to its partnership with Amazon. And even though that alliance could mean that you can look around for your chosen devices from almost any brand, the extensive line-up of Ring means you do not have to. With that said, you can select from a mile-long list of options for safety detectors, security lighting, cameras, and doorbells. Moreover, there are three plan options offered by Ring. The first plan is the free one that comprises all Ring purchases.
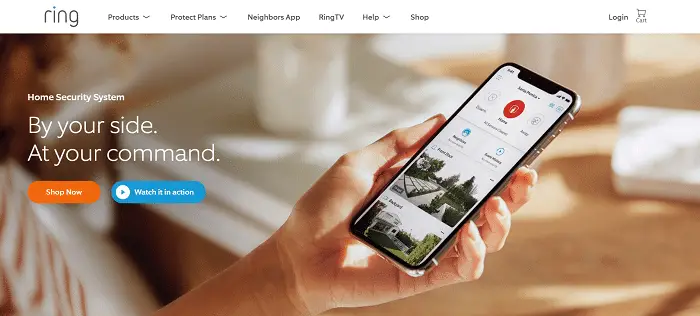 Therefore, you do not have to pay for the gadgets to operate or function: provide real-time access to your footage, send alerts, and detect motion. If you want professional monitoring or record video, you must move on from the Protect Plus plan or Protect Basic. Still, both plans are inexpensive. The last plan is professional monitoring, which costs at least 10 dollars per month. Moreover, Ring offers a video doorbell. It is where the security system company started; thus, the name. However, if you want to leverage this smart doorbell, you must pay for a monthly subscription. Remember that without it, you’ll only have real-time footage; there’s no video storage. In our list of best self-monitored home security systems, this system will surely give you peace of mind.
Therefore, you do not have to pay for the gadgets to operate or function: provide real-time access to your footage, send alerts, and detect motion. If you want professional monitoring or record video, you must move on from the Protect Plus plan or Protect Basic. Still, both plans are inexpensive. The last plan is professional monitoring, which costs at least 10 dollars per month. Moreover, Ring offers a video doorbell. It is where the security system company started; thus, the name. However, if you want to leverage this smart doorbell, you must pay for a monthly subscription. Remember that without it, you’ll only have real-time footage; there’s no video storage. In our list of best self-monitored home security systems, this system will surely give you peace of mind.
Visit: Ring Alarm
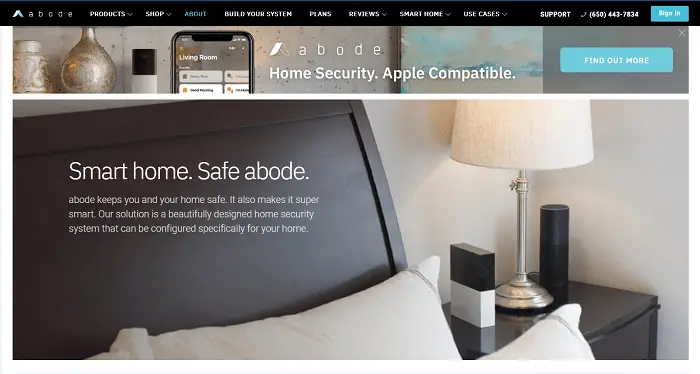
Abode Connected Home Security
If you are looking for entirely DIY or free self-monitoring, then Abode Connected Home Security System offers what you want. With all the appropriate tools and devices to make DIY home security more effective. The basic plan is included in every starter kit at zero cost. For under 10 or 20 dollars per month, respectively, you can upgrade to the Connect or Secure plan for professional monitoring and 4G cellular backup. With this security system, you don’t need to pay for professional monitoring services to access rewarding benefits. With the basic self-monitoring security system plan, you can control or regulate your home security system through a web or phone application.
Then, you can check recorded footage for about three days. Take note that most free storage plans are limited to only 24 hours. Moreover, this security system can connect over 160 devices to create or construct a truly automated home. That broad compatibility could be very beneficial since Abode works with Zigbee, Z-wave networks, IFTTT, Google Home, and Amazon Alexa. However, unlike Ring, Abode does not offer video doorbells. Remember that video doorbells are among today’s most efficient intelligent home gadgets. It serves as a daily tool for greeting visitors and a security measure. You don’t need to worry about the security of your home while using one of the best Self Monitored Home Security Systems.
Visit: Abode Connected Home Security
SimpliSafe
SimpliSafe intelligent home security system protects your house from intruders; It is a DIY security setup. It protects your house with simplicity and flexibility while allowing you to watch everything remotely with (or without) a monthly subscription. Its security systems also send alerts for natural disasters, fires, etc. SimpliSafe is the perfect blend of high-quality service, convenience, and value. 
It allows you to install a security system in under 60 mins. It’s simple to learn how to operate, and there are no commitments to sign to obtain access to affordable 24/7 monitoring plans. This security setup is worth every penny for outdoor cameras with two-way audio and alarm system.
Vivint
It offers 24-hour home monitoring with lightning-fast reaction times when an alarm is triggered and a choice of other home automation services that can all be handled from a smartphone, a PC, or the control panel. 
The Vivint system may be controlled remotely using free Android and iOS apps and from a PC via the web console. The mobile app’s home screen shows how many doors and windows are now open and which are unlocked.
ADT
What sets ADT apart is its customer service, with several ways to contact the help desk no matter what your issue is and response times that are almost instantaneous. 
You can see who is at the door and converse with them, adjust thermostats, turn on and off alarms, and more. Then there’s the online interface, which allows you to view account information and access your devices and is the only location where you can access advanced features like the new video analytics capability.
Wyze
DIY home security kits are a cost-effective method to monitor your house, but none are as cost-effective as Wyze’s new Home Monitoring system. Set it up quickly and secure your place and your family. The system can be accessed for free if you pay for a year of expert monitoring upfront. It’s compatible with Wyze’s intelligent home product line and third-party goods via Alexa and Google Assistant. Wyze Home Monitoring is economical, versatile, and easy to use.
 You must first download the mobile app. Then activate the service using the OTP sent to your email address. The setup page has menus for installing the hub, sensors, and any extra hardware, such as cameras. You can enter dispatch and monitoring data from the app.
You must first download the mobile app. Then activate the service using the OTP sent to your email address. The setup page has menus for installing the hub, sensors, and any extra hardware, such as cameras. You can enter dispatch and monitoring data from the app.
Abode iota Smart Security Kit
Consider the Abode iota Smart Security Kit to protect your home with an intelligent security system with a camera but on a budget. The Iota controls Wi-Fi, smart home devices such as door locks, garage door openers, water sensors, lights, and the camera. You can use voice commands with this security kit.
 The Iota performs well, and its HD camera also captures clear video in dark lighting. With voice control from Amazon Alexa and Google Assistant, HomeKit compatibility, and connection with most smart home gadgets. This one is a top contender.
The Iota performs well, and its HD camera also captures clear video in dark lighting. With voice control from Amazon Alexa and Google Assistant, HomeKit compatibility, and connection with most smart home gadgets. This one is a top contender.
FAQs
Which home security brands offer professional monitoring?
Several home security brands offer professional monitoring services, including ADT, Vivint, SimpliSafe, Frontpoint, and Brinks Home Security. These companies provide 24/7 monitoring by trained professionals who can respond to alarms and emergencies.
Which sensor is best for motion detection?
Passive Infrared (PIR) sensors are commonly considered the best for motion detection. They detect infrared radiation emitted by objects, making them sensitive to changes in heat signatures. PIR sensors are widely used in home security systems for their reliability and effectiveness in detecting human movement.
What is the most sensitive sensor?
In terms of sensitivity, it varies depending on the application. However, Magnetic (Hall Effect), Photoelectric, and Infrared sensors are highly sensitive in detecting specific parameters such as magnetic fields, light intensity, or infrared radiation.
How far can a 4k security camera see?
4K security cameras can generally provide precise details and capture recognizable images at distances of up to 250 feet or more, depending on the specific camera model and lens configuration.
Conclusion
An automatic home contains different intelligent devices, from environmental controls, lighting, sensors, and cameras, and for all that, one should have uninterrupted electricity to a property. However, without a single interaction method between them, you likely won’t achieve a smart home. Thus, when choosing a self-monitoring security system for homes, you must pick your protocol or platform. The protocol is the language the gadgets utilize with each other.
Other than that, weigh the significance of a self-monitored security system. Ultimately, you can easily set up the home security systems listed in this article or have a professional get everything up and functional. Also, remember that the kind of monitoring you select is essential. It must keep your family safe and fit your lifestyle.